Hack stories
Bybit: when hackers target people, not systems
Mon, 24th Mar 2025
#
mfa
#
blockchain
#
cybersecurity
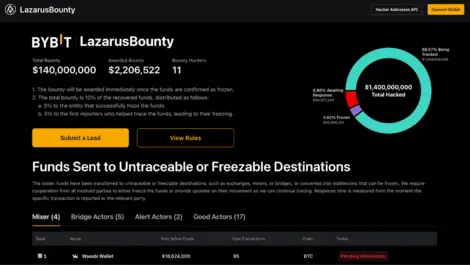
Bybit suffered a major hack, exposing vulnerabilities from human error rather than blockchain flaws, as attackers manipulated staff to divert funds.

Marketing vs. reality – What we can learn from the Ashley Madison hack
Fri, 5th Jul 2024
#
breach prevention
#
data breach
#
online dating
The Ashley Madison hack exposed the stark reality behind glossy marketing, revealing how a poorly safeguarded system endangered millions of private lives.

Australia’s National Cybersecurity Act races against technological advancement
Mon, 3rd Jun 2024
#
data protection
#
encryption
#
advanced persistent threat protection
Australia's fragmented cybersecurity laws face overhaul as new National Cybersecurity Act aims to modernise protection against AI and quantum computing threats.

New year, time to update your passwords
Thu, 7th Jan 2021
#
hack
#
passwords
#
nordpass
The most popular passwords of 2020 were easy-to-guess number combinations, such as 123456, the word password, qwerty, iloveyou, and other uncomplicated options.

Houseparty denies security breach as users accuse app of hacking accounts
Tue, 31st Mar 2020
#
cybersecurity
#
hack
#
cybersafety
The popular face-to-face video hosting service has been accused of hacking users' other accounts, a claim Houseparty disputes.

Australian women-focusd hackathon #SheHacks expands across Victoria
Fri, 28th Feb 2020
#
hackers
#
hack
#
hacking
Women-focused hackathon #SheHacks, run by Girl Geek Academy, will take place statewide across Victoria, Australia from February to April.

Teens prove IoT device vulnerabilities by hacking them
Fri, 1st Feb 2019
#
iot
#
cybersecurity
#
printing
After two teens managed to hack hundreds of thousands of printers around the world, KYOCERA Document Solutions has some tips for businesses.

NASA got hacked (again)
Thu, 20th Dec 2018
#
breach prevention
#
cybersecurity
#
data breach
The compromised servers stored personally identifiable information (PII) belonging to current and former NASA employees.

Surprise - the PyeongChang Winter Olympic Games were hacked
Mon, 12th Feb 2018
#
breach prevention
#
cybersecurity
#
data breach
Games organisers have reportedly admitted that its servers had been attacked, forcing them to shut down the official website.

Mega breach: 800,000 Swisscom customers’ data stolen via hacked partner
Fri, 9th Feb 2018
#
breach prevention
#
cybersecurity
#
hackers
Experts say while Swisscom may be playing the huge breach down, the implications of the breach will be far and wide.

How to keep your company safe from complex cyber threats
Mon, 6th Nov 2017
#
sonicwall
#
hack
#
computers
An advanced persistent threat is a set of stealthy and continuous computer hacking processes, designed to be evolving, polymorphic and dynamic...

Carbon Black and IBM Security tighten partnership with rapid response tool
Tue, 17th Oct 2017
#
hack
#
ibm security
#
carbon black
An expanded partnership between Carbon Black and IBM Security aim to provide increased cyberattack visibility and accelerated incident response times.

Yahoo's 2013 data breach hit all three billion user accounts
Wed, 4th Oct 2017
#
breach prevention
#
cybersecurity
#
yahoo
Yahoo’s entire user base of more than three billion people were affected by Yahoo’s colossal data hack in 2013, despite initial reports.

Security firm reveals Asia connections behind the CCleaner hack
Tue, 26th Sep 2017
#
advanced persistent threat protection
#
supply chain
#
hack
The attack was never intended for consumers, but instead went after companies such as NEC, Samsung, Asus, Fujitsu, Singtel, Intel and VMware.

Oh, sweet revenge: White hat hacker floods scammers' phone lines
Mon, 26th Jun 2017
#
email security
#
cybersecurity
#
scams
What happens when you put cold call scammers up against a seasoned programmer? You get sweet revenge, if the case of one security developer.

GovHack 2015 – Innovating with government data
Mon, 29th Jun 2015
#
data analytics
#
martech
#
planning
What do Twitter, GroupMeet and Facebook’s Like button all have in common? They all were invented at a hackathon.

Software developer duo hack Dropbox
Mon, 2nd Sep 2013
#
edutech
#
cloud services
#
dropbox
Cloud storage provider Dropbox has reportedly been hacked by two software developers, who bypassed its two-factor authentication.

How to bork your hard drive with HTML5
Fri, 1st Mar 2013
#
martech
#
software development
#
browsers
Discover how an HTML5 glitch, made public by Michael McKinnon of AVG, could fill your hard disk, revealed at http://www.filldisk.com/.

Frequent Facebook hacks no big deal
Mon, 18th Feb 2013
#
malware
#
cybersecurity
#
personal computing devices
Despite a sophisticated attack last month, Facebook says no user data was compromised, attributing its success to a robust security response and culture.

Twitter hacked - up to 250,000 accounts compromised
Sat, 2nd Feb 2013
#
encryption
#
martech
#
cybersecurity
Twitter blogged yesterday that an attack took place over 'just a few moments' before it was noticed by Twitter staff and shut it down.